While we wish we could show you how to really accomplish true privacy on Facebook, the only way to actually reach that threshold would require you to have never signed up in the first place. This doesn’t mean, of course, that there is nothing that you can do now to protect your information - sharing more cognizantly and keeping it within circles you trust.
A Few of Facebook’s Issues
Like we said, Facebook has seen some pretty egregious security issues during its time. While we aren’t going to go too far into the weeds with these events, a quick summary might help to illustrate how careful users should really be as they use the platform:
- In 2007, Facebook introduced a feature that would allow companies to track purchases made by users and notify their friends of what they had purchased… without requiring any consent from the user.
- In 2011, the FTC charged Facebook for allowing private user information to be accessed by third parties, making this private information public without any notification.
- In 2013, Facebook introduced a Donate button that would allow users to make charitable contributions to such organizations. Unfortunately, a bug in the code allowed the email addresses and phone numbers of over six million users to be leaked.
- In 2014, Facebook actively experimented upon their users, testing their ability to manipulate their emotional states with the content the user is exposed to. Depressing content was prioritized to see if they could elicit depressed feelings. As it turns out, they can.
- In 2015, Facebook took action to assuage their users’ concern for their privacy, and rolled back the access that apps had to user data… but one has to wonder, just how much were applications privy to before this rollback?
- In 2018, Facebook suffered a massive data breach, losing the data of 50 million users. In response, Facebook did nothing… that is, until their reputation started to suffer. It was only then that they responded to the underlying issues.
Unfortunately, concerning events like these happen far too regularly to Facebook. There just seems to be difficulty in keeping their user data secure. This is why you need to pay particular attention to the settings on your own Facebook profile. Let’s go over how your information can most effectively be protected by ensuring these settings are configured properly.
Configuring Your Facebook Privacy Options
On your desktop, log in to your Facebook account. At the top-right of the page, there will be a small down arrow. Click it to access a menu, then click Settings.
You will be brought to another page, with Privacy in your list of options. Click into it.
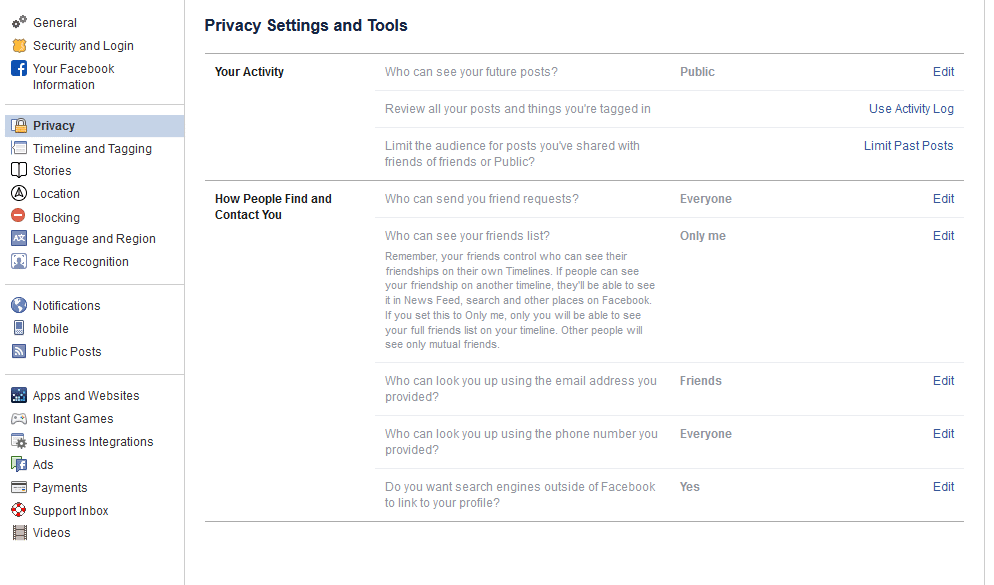
From here, you can set your privacy options that restrict who has access to your information. For example:
Public - Setting your privacy to public is effectively turning off your privacy options. Not only can all other Facebook users potentially see your profile, even people who aren’t signed in could access it. Hypothetically, this means that the search engines could find you are well.
Friends - This setting restricts viewing privileges to only your confirmed Facebook friends.
Friends except… - If there are particular friends or members of a particular group who shouldn’t see certain information, you can prevent them from seeing this on their Facebook.
Only me - This means that (outside of Facebook) you are the only person with access to what you have posted. Just to be safe, we recommend that you still refrain from sharing anything that you wouldn’t be comfortable sharing publicly.
You also have the ability to choose the audience for each individual post. While this may give the impression of improved control over your privacy, the biggest threat to your Facebook security is probably Facebook itself.
Of course, that doesn’t mean that you aren’t given plenty of privacy options to play with. Let’s go over some of them now:
Who can see your future posts? This setting establishes a default privacy setting for the content you post on Facebook in the future. This helps insulate you from sharing content out to those who shouldn’t see it.
Review all your posts and things you’re tagged in. By using the Activity Log, you can review the entirety of your timeline and manage the permission settings of past posts. You can also review posts you have been tagged in from here.
Limit the audience for posts you’ve shared with friends of friends or Public. This is a semi-nuclear option when it comes to locking down what you’ve posted in the past. By clicking Limit Past Posts, you can change all of what you posted publicly or to friends of your friends to only be accessible to those on your Friends list. Fair warning - Facebook doesn’t provide any way to revert this, so you would have to go through your posts by hand to change them back if you so wished.
Who can send you friend requests? Depending on your preference, you have the option of picking between Everyone or Friends of friends. Unlike many of the other settings on this list, leaving this set to Everyone is probably okay.
Who can see your friends list? On the other hand, there is no reason that the rest of the world needs to see who you are connected with on Facebook. Setting this to Only me will keep this information between you and Facebook, nobody else.
Who can look you up using the email address you provided? Do you want someone who has your email to be able to find you on Facebook using it? Most likely not - so restricting this to Friends or Only me is probably in your best interest.
Who can look you up using the phone number you provided? Again, it’s really your call whether or not to allow Facebook users to find you via your phone number, but it really isn’t that necessary. You’re fine setting this to Friends or Only me.
Do you want search engines outside of Facebook to link to your profile? This one really depends on your situation. Facebook can work to prevent the assorted search engines out there, including Google and Bing, from indexing your profile (allowing searchers to find it). Most people will likely want to switch this off, but if your personal brand is part of your business, it makes more sense to turn this option to Yes.
Dictating What Others Can Do On Your Personal Facebook Profile
We all have embarrassing friends, and so you may want to avoid having them be able to freely post content to your wall - for instance, your college buddy Greg seems to have no problem with sharing candids from the good ol’ days… and tagging you in them.
Potential situations like this make it all the better that Facebook gives you control over who can post to your timeline, and who can see this content. You can access your many options to do so by clicking into Timeline and Tagging (which can be found on the left side of your Settings).
Who can post on your timeline? Naturally, you will definitely want to put a limit on this, as there is no reason that a total stranger should be reaching out on your personal profile. This is why it makes sense to only allow your Friends to do so - or, perhaps you alone with the Only me setting.
Who can see what others post on your timeline? This setting will largely depend upon who you have permitted to post on your timeline. If your Friends can post to your timeline, you definitely want your Friends to be the only ones who can see it - assuming you don’t want to maximize your privacy (and hedge your bets) with the Only me setting.
Allow others to share your posts to their stories? Ask yourself: do you want anything you post publicly to be shared by your Friends? If so, leave this one enabled.
Who can see the posts you’re tagged in on your timeline? Tagging can be an incredibly useful thing for someone trying to cultivate an image as an engaged thought leader, but it can also hurt your reputation, never mind your privacy. If people keep tagging you in assorted posts and you’d rather the public at large didn’t see these posts, you can keep these posts to your Friends, or even to Only me.
Review the posts you’re tagged in before the post appears on your timeline?
Alternatively, this is likely the best option for someone looking to be visible via tagged posts, while still remaining in control of which posts that are linked to them. Basically, you can be notified if you are ever tagged in some Facebook content, and can opt whether or not it will appear on your timeline. Fair warning - any mutual friends you have with the person who has tagged you will be able to see the tagged content before you have a chance to review it. Regardless, it is best to keep this setting on.
Review tags people add to your posts before the tags appear on Facebook? Again, this is something you’ll want control over, so set this to on as well.
Managing Your Public Post Settings
Again, from the Settings page, click into the Public Posts option on the left-hand side.
Who Can Follow Me - Rather than adding users as Friends, public figures can provide the option to just be followed by interested people. If you want to give the public at large this option, set this to Public. Otherwise, you can keep your posts among your Friends by setting this to Friends.
Public Post Comments - Or, who can comment on the posts that you’ve shared publicly. It is probably best to keep this restricted to either Friends, or perhaps Friends of Friends.
Public Profile Info - Some facets of your Facebook profile are generally available for anyone to see (like your name and profile picture). Who do you want to be able to comment on your profile picture? Keeping this capability restricted to your Friends or - maybe - Friends of Friends is probably best.
How Much Do You Want Facebook to Know About Where You Are?
Facebook has the capability to track your location history. While this information isn’t shared with your Friends or followers (beyond letting your Friends know that you are nearby), the only real reason we could come up with for Facebook to track this is to be able to target you with ads more effectively. Hopefully, that’s the reason, but even so, it is better to be safe than sorry. After all, Facebook has a history of data security missteps.
Again, starting from the Settings page, click where it says Location on the left-hand side. From there, you can see what Facebook already knows by requesting to View your Location History. However, to disable this, you’ll need to use the mobile application.
Using the Mobile Application to Turn Off Location
From the app, access the 3-bar hamburger icon (found at the top-right), and scroll down until you see Settings & Privacy. From there, you should access Privacy Shortcuts, where you’ll see a new area with various settings and documentation regarding Facebook’s identity controls.
Find Manage your location settings (you shouldn’t have to scroll to find it). Once there, you should:
- Turn off Location History (found in Location Access)
- Turn off Use Location (in Location Services)
- Find and disable Background Location
While you’re at it, you may as well delete your existing Location History.
Again, from within Privacy Shortcuts, select Manage your location settings and then View Your Location History. You will be asked for your password, and then you will see another 3-dot menu in the top-right. From there, you should Delete all location history.
Take note: if you post a photo with your location tagged, or check into some public place, you may be allowing Facebook access to your location data again.
Yes, this is a lot to take in.
Thank you for sticking with us for so long! We hope this helps you to secure your personal privacy on what is known as the social network. To learn more about protecting your privacy and information, geared more toward your business, reach out to Coleman Technologies at (604) 513-9428, and make sure to subscribe to our blog.